以最近在西湖论剑上碰到的题目,TinyNode来记录下libc2-33下,house of pig的利用流程
0x01 house of pig
1.1 利用条件
- 至少存在uaf
- 程序可通过某种方式退出
- 当 libc 执行abort流程时。
- 程序显式调用 exit 。
- 程序能通过主函数返回。
1.2 利用思路
house of pig的利用思路就是,利用一个堆地址任意地址写,将_IO_list_all或者某个IO_FILE的chain字段,覆写为一个我们可以控制的堆地址,并在这个堆地址上伪造IO_FILE结构。当程序退出前会调用_IO_flush_all_lockp函数来flush所有IO流,当flush到我们伪造的IO_FILE结构时因为其参数和结构都是我们可控的,因此可以达到劫持控制流的目的。
在该堆地址构造 FILE 结构的时候,重点是将其vtable由 _IO_file_jumps修改为 _IO_str_jumps,那么当原本应该调用IO_file_overflow的时候,就会转而调用如下的IO_str_overflow。而该函数是以传入的 FILE 地址本身为参数的,同时其中会连续调用 malloc、memcpy、free 函数(如下图),且三个函数的参数又都可以被该 FILE 结构中的数据控制。
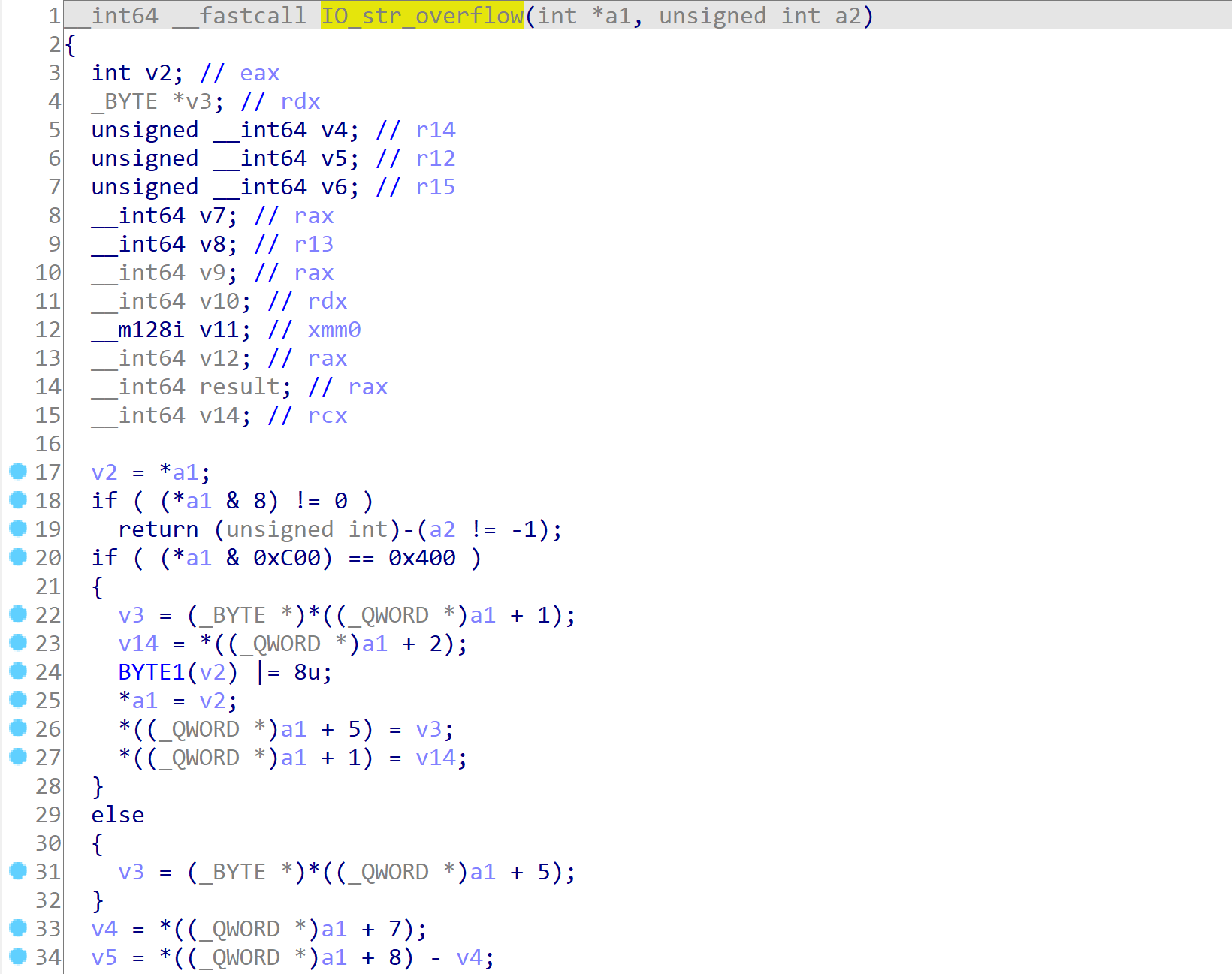
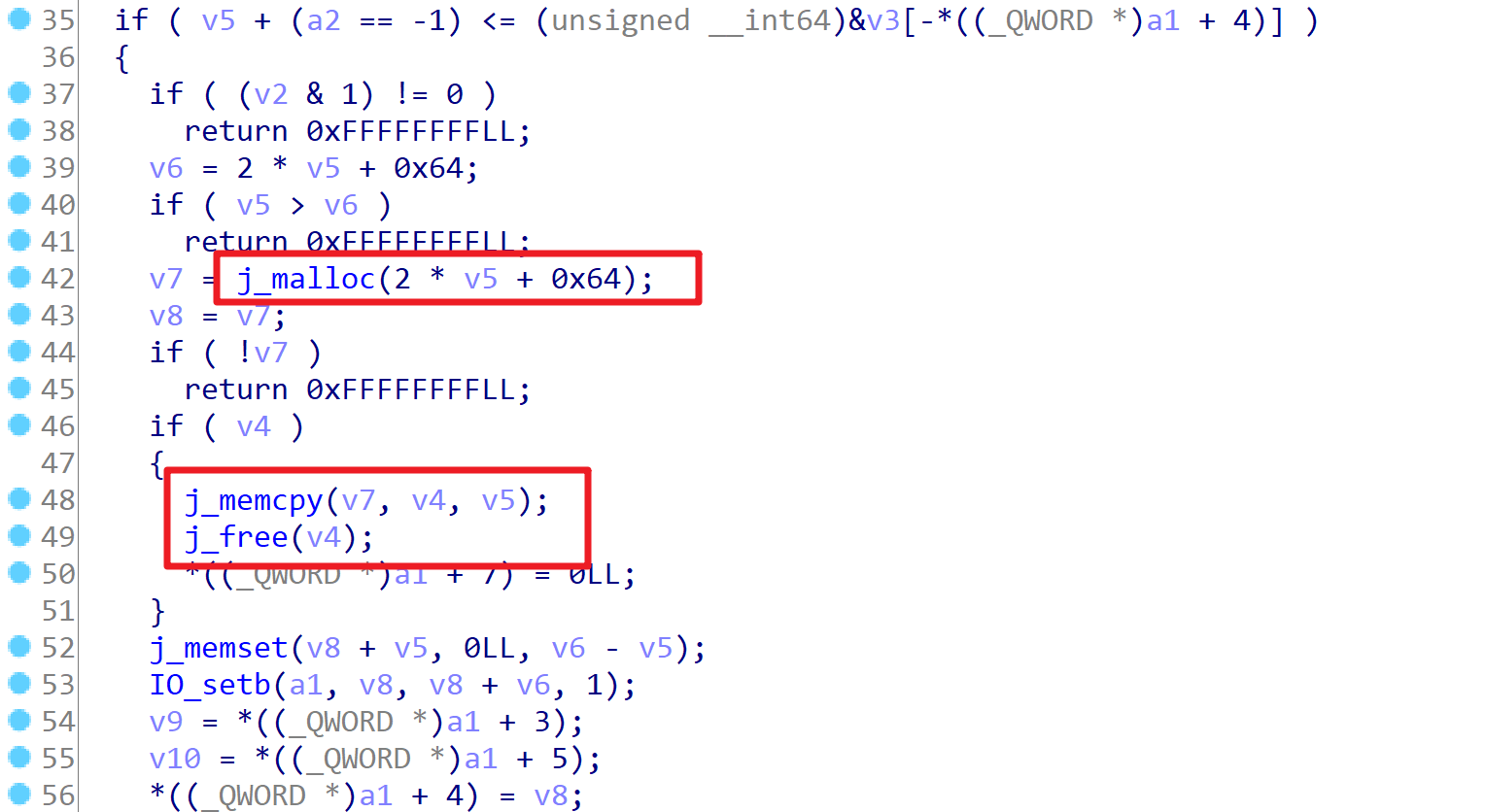
我们可以先通过malloc把提前放在tcache里的__free_hook取出来,然后利用memcpy将__free_hook修改为setcontext + 61,后面再调用free_hook触发SROP执行mprotect,再跳转到shellcode上完成整个orw的过程。
1.3 libc2-33新增的保护
除了2.32增加的对tache的指针进行一个异或它本身地址右移12位的操作之外,还新增了申请新地址时必须满足0x10对齐的限制。
0x02 西湖论剑2021 TinyNote
2.1 题目分析
main
大概来看有四个功能,add,show,edit,delete
1 | void __fastcall __noreturn main(__int64 a1, char **a2, char **a3) |
add
add功能是只可以申请0x10大小的chunk,而且sub_141E函数对malloc进行了一个封装,禁止我们申请堆空间以外的地址。
1 | int add() |
show
show没什么好说的,中规中矩的一个泄漏
1 | int sub_15B1() |
delete
存在uaf漏洞,free之后没有把指针清空
1 | void sub_1626() |
2.2 利用分析
- 利用uaf首先把heap地址和libc地址泄漏出来
- 因为只能申请0x10大小的chunk,因此利用[fastbin_reverse_into_tcache](house_of_botcake && fastbin_reverse_into_tcache | 木头的小木屋 (wood1314.github.io))进行一个任意地址写堆地址。这个时候由于libc2-33的对齐保护,所以_IO_list_all是不能劫持的,stderr等也不能直接劫持,只能选择
_IO_2_1_stderr的chain字段,利用我们tcache的key来劫持,正好可以劫持到heapbase+0x10的位置。这里不用fd字段劫持的原因是,fd字段会被抑或成一个很奇怪的字段,影响后续利用。 - 伪造IO_FILE结构,劫持控制流执行orw
2.3 利用过程
预备工作
使用patch-elf修改题目libc为对应版本的glibc-all-in-one中的libc,方便带符号调试
1 | patchelf --set-interpreter /home/wood/glibc-all-in-one/libs/2.33-0ubuntu5_amd64/ld-2.33.so ./TinyNote |
泄漏heap 地址和libc 地址
1 | from pwn import * |
构造fake_FILE
1 | IO_str_vtable = libc_base + 0x1e2560 |
为后面的利用提前布置一些地址
1 | # put free_hook on tcache in 0x80 size |
设置SROP的frame以及shellcode
1 | # set frame |
构造 fastbin_reverse_to_tcache
这里注意要把fastbin填为8个,这样的话就不会在reverse_into_tcache的时候引入别的chunk。
1 | # #Create a fake fastbin chains |
在此时fastbin的状态如下

然后
1 | Add(0) |
大胜利!

0x03 完成exp
1 | from pwn import * |
0x04 附件
链接: https://pan.baidu.com/s/1okMdhQF0z8RQmEOCQM6eng 提取码: 5871